Let’s take a dive into a threat policy strategy for Exchange Online Protection and how to effectively implement them in your environment.
What are Threat policies?
Threat policies are part of Exchange Online Protection. Everyone with a Microsoft 365 license can use these policies to protect their environment against various kinds of threats. There are five different category threat policies you can define:
- Anti-phishing – Protect users from phishing attacks and configure safety tips on suspicious messages.
- Anti-spam – Protect your organization’s email from spam, including what actions to take if spam is detected.
- Anti-malware – Protect your organization’s email from malware, including what actions to take and who to notify if malware is detected.
- Safe Attachments – Protect your organization from malicious content in email attachments and files in SharePoint, OneDrive, and Teams.
- Safe Links – Protect your users from opening and sharing malicious links in email messages and Office apps.
If you want to know more about threat policies and what they can do, you can start reading all about it here: Exchange Online Protection (EOP) overview | Microsoft Learn.
In this article I’ll wright about a simple approach on how to implement a threat policy strategy and how to tailor them to your organizational needs.
The Threat Policy Strategy
All threat policies work with priorities. meaning that the policy with the highest priority (0) will be applied first and the lowest priority will be applied as last. The second thing you need to know is that threat policies can be assigned to everyone, domains, groups and even users. And the last thing you’ll need to know is that once a policy has been hit for a recipient, the other policies won’t apply.
If your organizational needs require you to configure multiple anti-malware policies, the strategy to design of a full set of threat policies will need to follow this approach:
| Priority | Policy Assignment |
| 0 | User-based policies |
| 1 | Group-based policies |
| 2 | Domain-based policies |
| Lowest | Default policy |
With this approach, policies tailored to individual users (most specific) take precedence over policies designed for groups or domains to which the same user may belong (most generic). This hierarchical arrangement creates a cascade effect, ensuring that policies are applied in a sequential and prioritized manner.
Default policy
Default threat policies can’t be deleted or disabled. It shouldn’t be. These policies should be the baseline that is applicable for most recipients in your organization.
Together with the security team and other stakeholders you can decide what configuration should be set as a baseline that will be applied to all messages.
Note: For most organizations one policy per category (anti-malware, anti-phishing, etc.) is sufficient to fulfill all business needs. In that case you can alter the default to the requirements and you’re all set.
Domain-based policies
Larger organizations often work with multiple domains to differentiate subsidiaries or because of one or more mergers.
If applicable, you can choose to configure threat policies that are tailored to the users who are part of a specific domain.
Group-based policies
Groups often define teams, departments, or locations. Each can have their own requirements regarding threat policies. Think about e.g., compliance requirements.
If a group has a common denominator, you can configure and apply their own threat policies.
User-based policies
High targeted users who have high value or importance within an organization often require strict threat policies. In that case you want to implement user-based policies which are tailored to the requirements of the user.
How does this look like in practise?
In below picture you see a set of anti-malware policies based on this strategy.
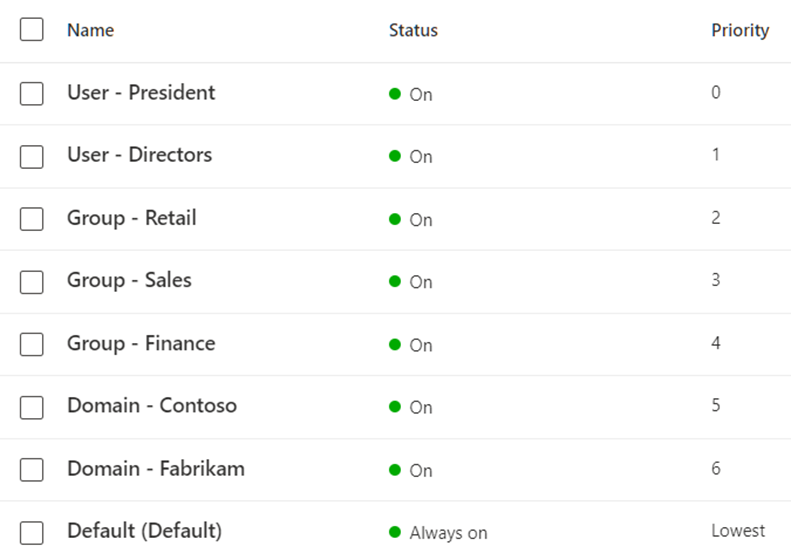
So, there you have it, a threat policy strategy for Exchange Online Protection. A simple, yet effective strategy to apply multiple threat policies for your organization. What kind of strategy did you use? Leave your tips and tricks in the comment.
Leave a Reply
You must be logged in to post a comment.